Attempts to exploit our newsletter subscription process to send spam (part 1)
The problem
A few days ago, we started noticing on our main websites (www.threatint.com, cve.threatint.com) that about 400 to 500 email addresses were subscribing to our newsletter every day without completing the second step of the subscription process. Most of the recipients didn't click on the link in our confirmation email, but about 5% of our confirmation emails bounced, so these recipients potentially never existed in the first place.
We could not draw any conclusions from the email addresses used. Most of them were from platforms like Gmail or Yahoo, but there were also other domains.
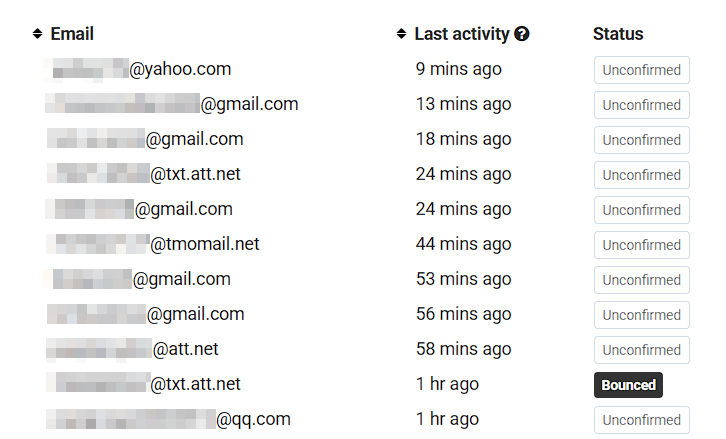
All attempts were coming from different IP addresses, which would be typical for botnet activity. But one thing caught our attention: they did not try to deliver 1000, 10,000 or 100,000 emails in a short amount of time - this is what usually happens when threat actors find an exploitable service. We do have some rate limiting rules in place, but these rules were not triggered, so we are confident that they really only tried to deliver a small number of emails. We currently have no idea why they were so hesitant. And what were they trying to achieve.
How do people subscribe to our newsletter?
We tried to design the process of subscribing to our email newsletter on our main websites as frictionless as possible while also complying to regulations like the EU-GDPR: you go to one of our websites, scroll to the end of the page, enter your email address, and press [Return] - there are no other fields! A 'thank you'-message will be shown and you will be sent a confirmation email that asks you to click two more times before you are actually subscribed to our newsletter. This is called double-opt-in.
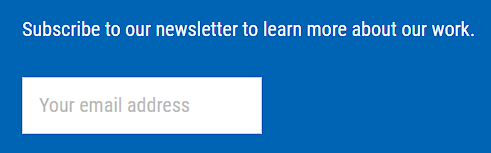
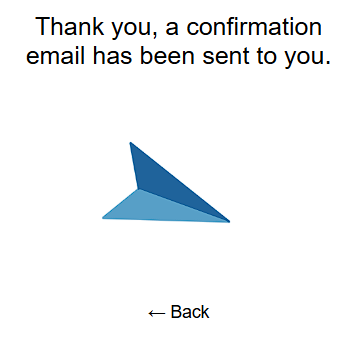

How do spammers operate?
If there were other field e.g. a comment, spammers would paste their content into that field and use random email addresses to have our service send emails with a confirmation but also with the content provided by the spammer in the comment. It's not ideal, but it's a way for spammers to get their message out into the world, so that's what they might go with.
What does this mean for us?
But: there are no other fields on our sites! So unless the goal was to lower our reputation score with our email providers (side note: we use Amazon SES and Mailgun, both have an eye on the score), there is nothing to be gained because no additional content gets delivered.
Have you seen similar patterns on your website? We would love to hear from you.
